Spear Phishing and How to Protect Your Company
Spear Phishing is a major issue causing small and medium-sized businesses billions of dollars in fraud. Find out what it is and how you can protect yourself from it.
Example of Spear Phishing
Pam is the Director of Marketing for an international firm. Recently she received an email from the CEO. In the email, the CEO asked her to purchase ten $100 Walmart gift cards. Further, the email stated that the gift cards were a reward for her team doing a good job on a recent project. Certainly, Pam was thrilled the CEO called her for such an important task.
Quickly, Pam ran down to Walmart and purchased 10 gift cards. Shen then followed the instructions and emailed him both the gift card and pin numbers. Unfortunately, the expense was flagged and Pam found out she was a victim of a Spear Phishing attack.
What is Spear Phishing?
Spear phishing is when someone uses a false identity to target an individual. Subsequently, the sender always appears to be a well known and trusted source. For example, it could appear to come from the target’s executive, boss, or trusted business partner. As expected, it always involves money or clicking a link. The most common include:
- Brand Impersonation – When a hacker impersonates a well-known company. One popular example of this is an email from a financial institute that claims there is an issue with your account. These emails look very legitimate. The most common are emails from Microsoft or Apple stating there is an issue with your account.
- Business Email Compromise AKA CEO Fraud – This is when someone impersonates a C-level executive and requests the sender to wire money, transfer funds, or buy something like gift cards.
- Blackmail Scams – When someone claims to have compromising information on you and threaten to expose you if you do not pay them.
How Do These Scams Work?
Scammers are smart. For instance, with Brand Impersonation or Business Email Compromise: they research the business, their employees, types of transactions, and those in authority. Next, they establish an email address that is similar to one of the authority figures. Finally, they email an employee with access to funds or company credit cards and request something that would not be suspicious or questioned by that employee. On the other hand, Blackmail Scams cast out a wide net in hopes to catch more prey.
7 Technologies That Can Protect Your Company
Clearly, hackers understand the general user’s weaknesses and how to exploit them. Therefore, the first step to eliminating this threat is to implement some basic technology tools. After all, if the end-user never receives the email, there is no way they can click on a bad link or respond to it.
- Artificial Intelligence Tools – Machine learning tools can analyze abnormalities and filter those emails.
- Spam Filtering – Spam filtering will help detect any malware embedded in the email, filter suspicious emails, and identify the origin country of the email.
- Antivirus – Antivirus will help detect and filter any viruses.
- DMark Authenticating – This technology authenticates the phishing email and puts it into the spam folder or rejects it.
- Email Encryption – Email encryption allows you to send and receive sensitive information over the Internet.
- Multi-Factor Authentication – This technology requires two pieces of identification to access company data.
- Desktop Monitoring – Desktop monitoring will keep your patches and updates current to keep hackers from accessing your email accounts.
5 Employee Training Tips on Spear Phishing
No matter what you do, some emails will still get through. Therefore, your greatest defense is to train your end-users. Make sure your employees follow the directions below before acting on anything that requests some form of sensitive information:
- The most important advice you can give to an employee is to study the sender’s email address. Often times, it is a single letter added or missing to the person’s name or domain. Do not click or act on anything until verified.
- Make sure the employee verifies the domain name of the sender. Do not click or act on anything until verified.
- Make sure all employees know that any request to spend money will come from company email addresses, not a personal email address. Do not click or act on anything until verified.
- Train employees to report any questionable phishing emails, texts, or voice mails to your IT department.
- Tell the employees, “When in doubt: ask.” Make sure they are not apprehensive about verifying an email from anyone in your company. Including the CEO.
INSI is Here to Protect You!
This post is part of the INSI Awareness Campaign that is designed to keep our clients protected and informed. In addition, you can click here to learn more about our security offerings.
Most importantly, if you are concerned about a spear-phishing email, please do not hesitate to contact our helpdesk at 770-387-2424 before opening it. Our engineers are more than happy to check it out and make sure it is safe. After all, we are here to serve you!






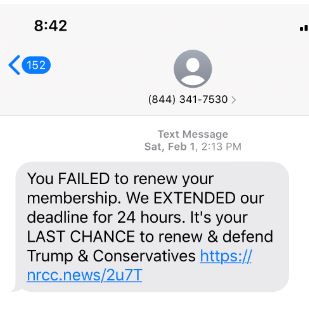 Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.
Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.