Smishing and How to Protect Your Cell Phone
What is a Smishing Email?
A smishing email is a general term for a text that requests for you to click on a link, respond, or provide personal/corporate information. The results of a successful smishing attack could mean compromised pin number, credit card information, passwords, social security number, and other private details that could lead to stolen identity.
What Types of Viruses Are Phones Vulnerable Too?
Interestingly, the types of viruses infested on phones are similar to the ones you see on computers. For instance, your phone can be compromised adware, malware, ransomware, spyware, or Trojan horses.
How Do You Avoid Becoming a Smishing Victim?
There are many ways you can arm yourself against smishing attacks. They include awareness, research, and avoidance.
1. Watch Out for Questionable Text
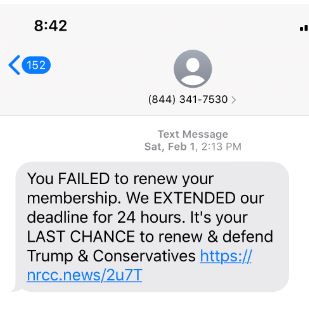 Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.
Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.
The second clue is an immediate call for action. Smishing texts will use emotional manipulation to try to get you to click or respond immediately. In this example, they are clearly aiming to use a scare tactic by using the word “FAILED” in caps.
In addition, smishing texts will often use banking information to solicit feedback. In some cases, they can even provide part or all of your account numbers. Make sure it is legitimate before clicking.
2. Google the Phone Number
When in doubt research the phone number. In this particular example, it was a car insurance company. Obviously, this is not the Republican party as suggested in the text above.
3. Be Wary of Location Awareness
Cybercriminals are smart! They can use the VPN app on your phone to reveal your location. Subsequently, they know that a local text is more personal and will often yield a response from their victims. For example, they can make it appear that you are receiving an offer from a local pizza parlor.
4. DON’T CLICK or Respond
Watch out for emails from unknown sources that ask you to click on something or respond. Both of these activities will download a virus on your device.
You should also beware of unsolicited emails from known senders with short subject descriptions or just a link. For example, that person in your church or networking group that you hardly know will likely not send you a text with just a link out of the blue.
How Do You Know if You Are Already Infected?
Your phone could already be infected without your knowledge. Here are some simple clues to find out if you are infected. Is your:
- Phone crashing a lot?
- Is the battery draining much faster?
- Phone showing new apps you didn’t download?
- Device showing an unexplained sizable increase in data usage?
- Phone company billing you for questionable text charges?
- Does the device receive pop-up adds?
- Phone overheating often?
How to Clean Up a Virus on Your Phone
To clean up a virus on your phone the first thing you need to do is clear the history and data. This should help with any type of pop-ups. Secondly, power off and restart your phone. Thirdly, restore from an earlier backup if the first two steps didn’t work. Last, restore as a new device as a last alternative.
Be Proactive About Smishing
The most important thing you could do to avoid a smishing scam is to download antivirus software on your phone. Many users believe their cell phones are immune to security threats, but that is not true.
If You Think You Have A Smishing Text – Let Us Know
This post is part of the INSI Awareness Campaign that is designed to keep our clients protected and informed. In addition, you can click here to learn more about our security offerings.
Most importantly, if you are concerned about smishing texts, please do not hesitate to contact our helpdesk at 770-387-2424 before opening it. Our engineers are more than happy to check it out and make sure it is safe. After all, we are here to serve you!





