Network Security Risks: Your Clients, Vendors, and You!
Did you know the average hacker lives on your network for 9-months before being detected? That is 9 months of cybercriminals digging into your financials, human resources information, and intellectual property! Further, if your business is storing, accessing, or transmitting client or patient data, you legally responsible for securing those records. As a result, clients, prospects, and patients will now view you as a security risk for sensitive information.
History of Network Security for Small- and Medium-Sized Businesses (SMB)
In the past, managed security was unaffordable to SMBs. However, in recent years, the cost has come down significantly. More importantly, managed security technology has advanced tremendously. Therefore, small- and medium-sized businesses no longer have to rely on the basic block and tackle security techniques. Instead, they can now armor their network with the most advanced security measures.
Do Criminals Want SMB Data?
Remarkably, the average SMB CEO claims hackers are not interested in their small company. Yet, that is exactly what makes them a great target. According to the Ponemon Institute, 69% of targeted attacks were SMBs. Even more daunting is the fact that 60% of SMB businesses never recover from a severe cyberattack. Therefore, network security is a must-have for all businesses that rely on their data, regardless of size.
Are You Responsible for Your Clients’ Data?
Unfortunately, a lack of security does not just put your data at risk. In today’s world, many businesses are trusted with sensitive information that belongs to another company. For this reason, supply-chain network security has become a mandatory requirement for vendors who want to do business with enterprise or government entities. Specifically, these are vendors who have access to, transmit, or store their sensitive data.
Similarly, the HITECH Act requires all covered entities (healthcare providers) to adopt Business Associate Agreements. This can be found in the HIPAA Risk Assessment Administrative Safeguards. In short, this rule makes the vendors equally responsible for protecting patient data.
In addition, you should also take precautions if your business captures individuals’ personal information. Examples include:
- Credit Card/Debit Card Information
- Social Security Numbers
- Phone Numbers
- Addresses
- Drivers License Number
- Passwords
- Banking Information
- Your employees’ personal information
It is a good exercise to think through all the companies you share this information with. Examples include telemarketers, HR companies, data analysts, etc. Next, take precautions to ensure your vendors are safeguarding your company’s sensitive information.
Georgia State Security Breach Notification and Network Security
Interestingly, all 50 states have implemented Security Breach Notification Laws that require businesses to notify individuals when there has been a breach that involves personally identifiable information. Specifically, Georgia Security Breach Notification Law lists the types of data that make individuals most vulnerable. Additional requirements state a company “shall notify the information broker or data collector of any breach of the security of the system within 24 hours following the discovery.”
Therefore, it is not only in your best interest to perform a Risk Assessment on yourself, but also on every vendor you share sensitive information with. This is because regardless of who is at fault for the breach, your employees and clients will ultimately hold you responsible if you did not do your due diligence.
Root Cause of Most Data Breaches
Interestingly, negligent employees and contractors account for 62% of all data breaches. Unfortunately, Ponemon Institute 2019 Global State of Network Security report states, “The biggest problem is not having the personnel to mitigate cyber risks, vulnerabilities, and attacks (77 percent of respondents). The next biggest challenges are insufficient budget (55 percent of respondents) and management having no understanding of how to protect against cyberattacks (45 percent of respondents).” That is where INSI can help.
INSI Has Network Security Programs for SMBs
Fortunately, you do not have to go through this alone. INSI has comprehensive Managed Security packages to help protect your sensitive data. Examples include:
- Security Information & Event Management (SIEM) – 24/7 real-time threat monitoring, event correlation, and incident response.
- End-Point Managed Detection & Remediation (MDR) – The next level of anti-virus analyzes and monitors events on devices, detect threats, stops the threat, and guides you to remediation.
- Risk Assessments – Identify strengths, weaknesses, opportunities, and threats (SWOT) to your network by using policy-based frameworks.
- INSI Complete Security Package – includes a security audit, network security vulnerability assessment, semi-annual security check, biannual penetration test, phishing email test and training, quarterly security checks, staff training, antivirus monitoring, web content filtering, web protection, and spam protection.
Contact INSI today to find out more about our security offerings at 770-387-2424.
About INSI
Since 1995, INSI has been providing IT support to small- and medium-sized businesses (SMBs) in both Georgia and Alabama. We offer Managed Services and our own unique INSI Customized IT™ package. Additional services include hosting, disaster recovery, managed security and unified communications.





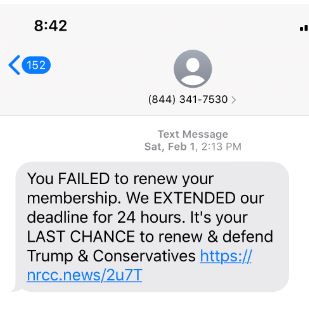 Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.
Clearly, this text example is an attempt to scam Trump supporters. Subsequently, smishing texts often claim to already have an existing relationship with you. Remember, if you are not sure don’t click or respond.
